Two Charged in SIM Swapping, Vishing Scams
Krebs on Security
NOVEMBER 3, 2020
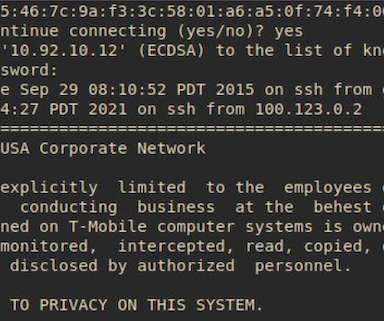
Two young men from the eastern United States have been hit with identity theft and conspiracy charges for allegedly stealing bitcoin and social media accounts by tricking employees at wireless phone companies into giving away credentials needed to remotely access and modify customer account information.















Let's personalize your content