macOS: Bashed Apples of Shlayer and Bundlore
Security Affairs
JULY 14, 2021
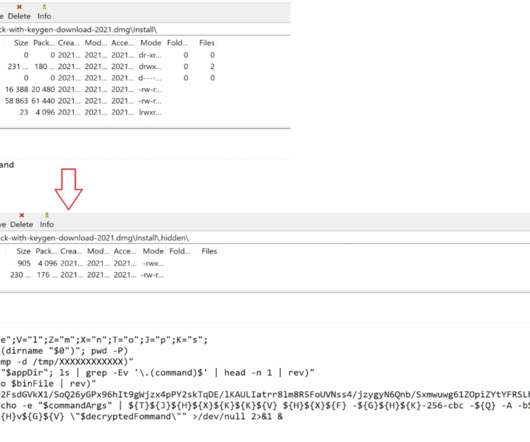
Though these scripts have slight variations, they mostly belong to a plague of adware strains— Shlayer and Bundlore. These malware are the most predominant malware in macOS, also with a history of evading and bypassing the built-in Xprotect, Gatekeeper, Notarization and File Quarantine security features of macOS.











Let's personalize your content