Hackers hijacked the eScan Antivirus update mechanism in malware campaign
Security Affairs
APRIL 24, 2024
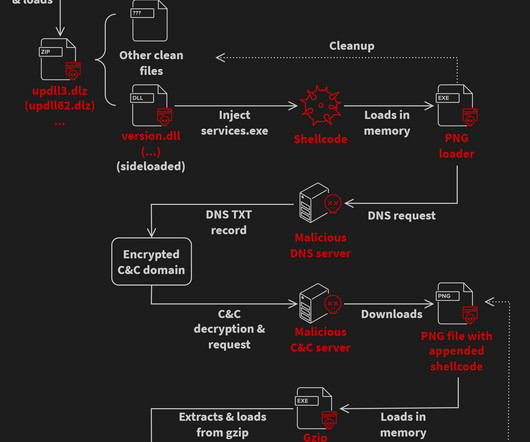
A malware campaign has been exploiting the updating mechanism of the eScan antivirus to distribute backdoors and cryptocurrency miners. Avast researchers discovered and analyzed a malware campaign that exploited the update mechanism of the eScan antivirus to distribute backdoors and crypto miners.














Let's personalize your content