GO#WEBBFUSCATOR campaign hides malware in NASA’s James Webb Space Telescope image
Security Affairs
AUGUST 31, 2022
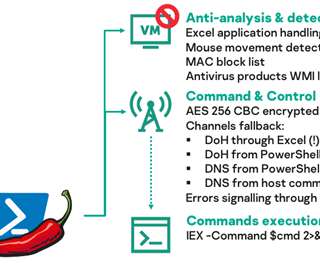
The phishing emails contain a Microsoft Office attachment that includes an external reference in its metadata which downloads a malicious template file. “This technique works by sending an encrypted string appended to the DNS query set as a subdomain. We have observed similar behavior with DNS exfiltration tools such as DNSCAT2.”















Let's personalize your content