Hiding Malware in ML Models
Schneier on Security
JULY 27, 2021
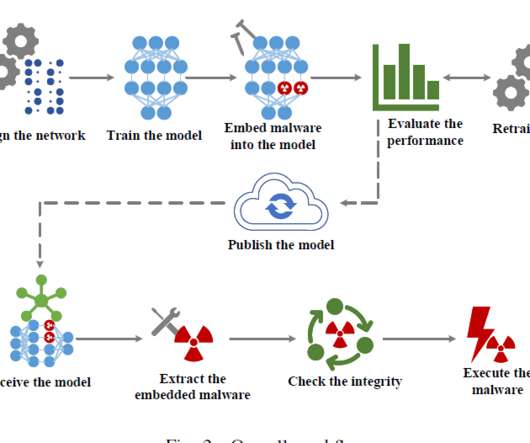
Interesting research: “EvilModel: Hiding Malware Inside of Neural Network Models” Abstract: Delivering malware covertly and detection-evadingly is critical to advanced malware campaigns. In this paper, we present a method that delivers malware covertly and detection-evadingly through neural network models.









































Let's personalize your content