Cybersecurity Predictions for 2023: My Reflections
Jane Frankland
NOVEMBER 20, 2023
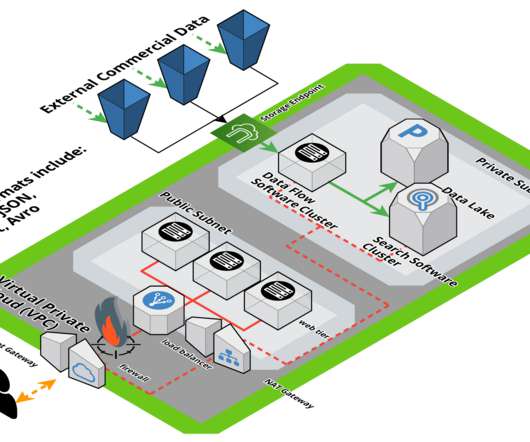
Nonetheless, cloud computing will continue to dominate digital transformation efforts, and many benefits will occur including enhanced data asset protection, fewer compliance failures, cyber resilience, and business productivity. Sustainability. More companies will be focused on sustainability.

















Let's personalize your content