The business case for security strategy and architecture
Notice Bored
AUGUST 8, 2022
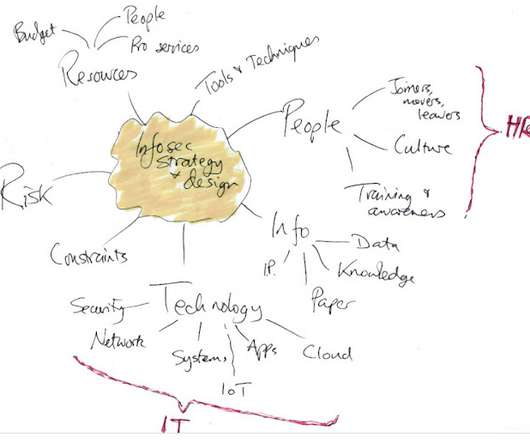
c omplementing and supporting various other business strategies and architectures such as cloud first, artificial intelligence, IIoT, big data, new products, new markets.); There are tools and techniques to help with strategy and architecture, just as there are for information risk and security management. Study hard.

















































Let's personalize your content