CISO workshop slides
Notice Bored
AUGUST 5, 2022
A glossy, nicely-constructed and detailed PowerPoint slide deck by Microsoft Security caught my beady this morning.

Notice Bored
AUGUST 5, 2022
A glossy, nicely-constructed and detailed PowerPoint slide deck by Microsoft Security caught my beady this morning.

SecureWorld News
MAY 6, 2025
CISOs and their teams operate in a high-stakes environment where every misstep can result in breach headlines, financial loss, or reputational damage. The cybersecurity industry has long since moved to a mental model of resilience when thinking about programs and architecture. In cybersecurity, the stress is relentless.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

IT Security Guru
SEPTEMBER 25, 2023
The IT Security Guru caught up with Tarnveer Singh a CISO and finalist in the Security Serious Unsung Heroes Awards 2023 for his thoughts on how to get more professionals involved in the cybersecurity industry: There are many ways we can inspire new cybersecurity professionals to join our industry. We must reduce barriers to entry.
Cisco Security
APRIL 20, 2021
Cisco Secure Endpoint and MITRE ATT&CK: Why it matters to CISOs right now. Cisco Secure Endpoint is security that works for your secure remote worker, SASE, XDR, and Zero Trust architecture. Securing your endpoints has never been more critical and you need endpoint security you can trust.
Cisco Security
APRIL 19, 2022
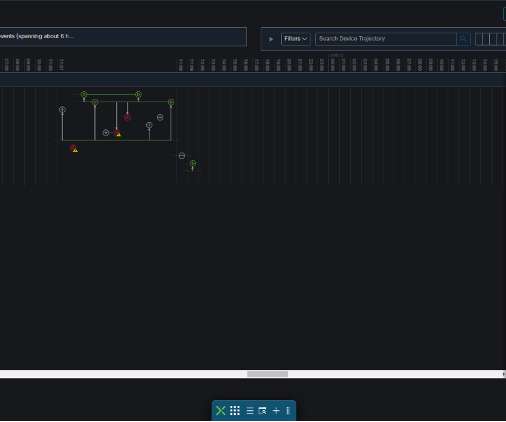
Cisco Secure Endpoint and MITRE ATT&CK: Why it matters to CISOs right now. Meeting security head-on requires adopting a comprehensive cloud-based endpoint protection solution for your secure remote worker, SASE, XDR, and Zero Trust architecture. Links to Cisco’s MITRE Engenuity ATT&CK results: Scenario 1: Wizard Spider.

CyberSecurity Insiders
SEPTEMBER 27, 2021
LEARNING: We will compare three of the industry's most popular architecture models: Zero Trust, Secure Access Service Edge (SASE), and Extended Detection and Response (XDR) to identify where they overlap, their key differences, and the unique value each offers businesses that want to modernize network. Build your SASE strategy.
Cisco Security
FEBRUARY 16, 2021
However, when you are assigning architectural controls to mitigate that risk, it lacks validation. Attend a Threat Hunting Workshop. Threat hunting is part the next evolution of risk management.”. It becomes evident that the Security Outcomes Study has something for every level of the corporate security chain. Beers with Talos Ep. #97:
Let's personalize your content