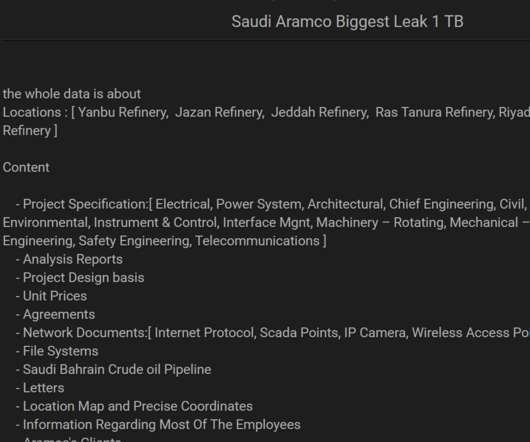
Threat actor claims to have stolen 1 TB of data belonging to Saudi Aramco
Security Affairs
JULY 19, 2021
This isn’t the first attack suffered by the Oil giant, in 2012 Saudi Aramco suffered a major cyber attack, alleged nation-state actors used the Shamoon wiper to destroy over 30,000 computers of the company. ZeroX is also offering a 1 GB sample for US$2,000 that could be paid in Monero (XMR) virtual currency.














Let's personalize your content