Cooking Intelligent Detections from Threat Intelligence (Part 6)
Anton on Security
DECEMBER 1, 2023
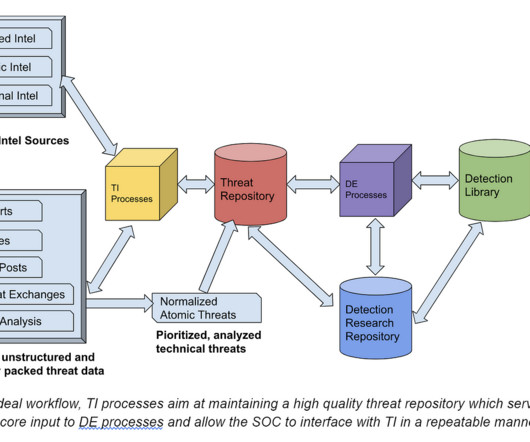
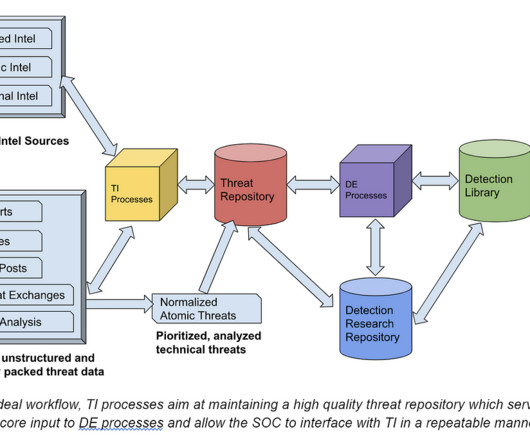
It provides the necessary context and insights for DE teams to effectively design and implement detection mechanisms that safeguard an organization’s valuable assets against evolving cyber threats. Working with other security related teams, such as Endpoint Security, Cloud Security, Security Architecture etc.








Let's personalize your content