New P2PInfect bot targets routers and IoT devices
Security Affairs
DECEMBER 4, 2023
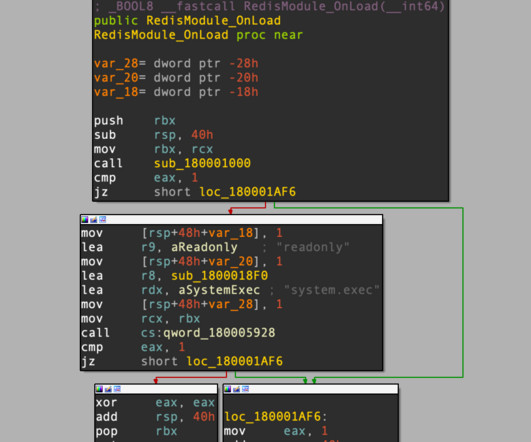
Cybersecurity researchers discovered a new variant of the P2PInfect botnet that targets routers and IoT devices. Researchers at Cado Security Labs discovered a new variant of the P2Pinfect botnet that targets routers, IoT devices, and other embedded devices. ” reads the report published by Cado Security.
























Let's personalize your content