The Evolution of SIEM: Where It’s Been and Where It is Going
CyberSecurity Insiders
NOVEMBER 7, 2022
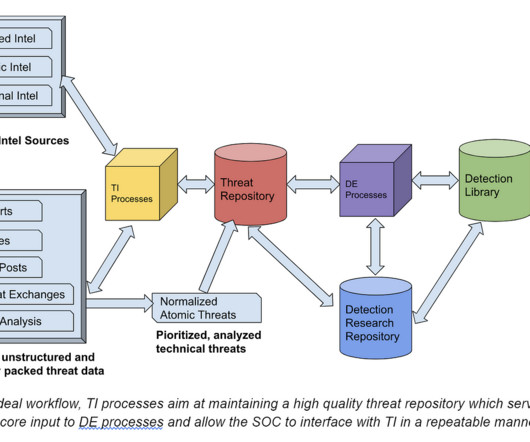
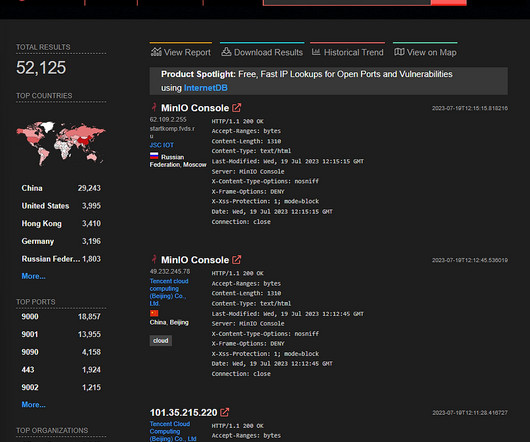
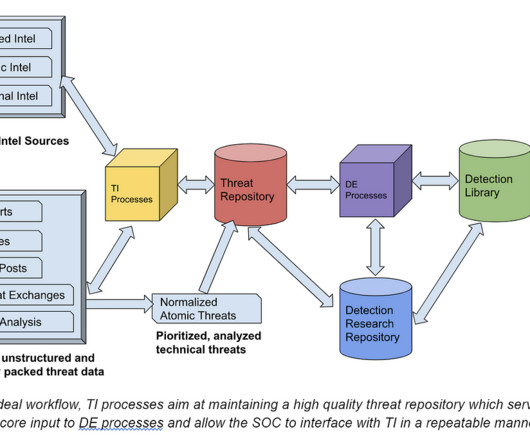
billion of total cybersecurity spending and is expected to increase to $6.4 This is easy to understand as SIEM has evolved into the data store for cybersecurity data which has been exploding as the volume of data and number of alerts is growing exponentially. Today, SIEM accounts for approximately $4.4










Let's personalize your content