Breaking Down User Activity Monitoring Tools: Security and HR Perspectives
SecureWorld News
JANUARY 4, 2024
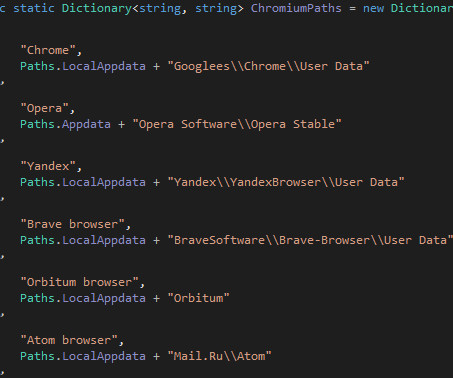
When and why companies implement UAM solutions UAM tools are often employed when a company's HR or information security departments identify specific issues that cannot be resolved by other means. On the flip side, employees often lack access to the data collected by UAM solutions.













Let's personalize your content