Cuttlefish malware targets enterprise-grade SOHO routers
Security Affairs
MAY 1, 2024
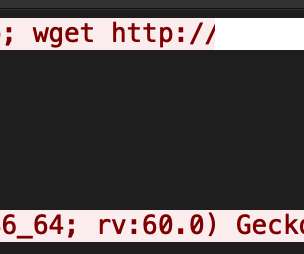
The malware creates a proxy or VPN tunnel on the compromised router to exfiltrate data, and then uses stolen credentials to access targeted resources. The malicious code can also perform DNS and HTTP hijacking within private IP spaces. The bash script also downloads and executes Cuttlefish. ” concludes the report.

















Let's personalize your content