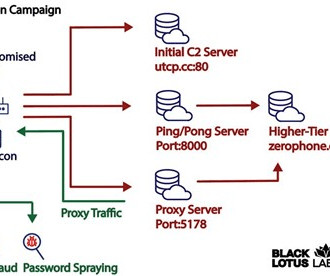
Experts link AVRecon bot to the malware proxy service SocksEscort
Security Affairs
JULY 31, 2023
The experts discovered that the malicious code had been compiled for different architectures. Operators behind SocksEscort offer for rent access to compromised residential and small business devices. The AVrecon malware was written in C to ensure portability and designed to target ARM-embedded devices. “ SocksEscort[.]com













Let's personalize your content