Passkeys and The Beginning of Stronger Authentication
Thales Cloud Protection & Licensing
FEBRUARY 1, 2024
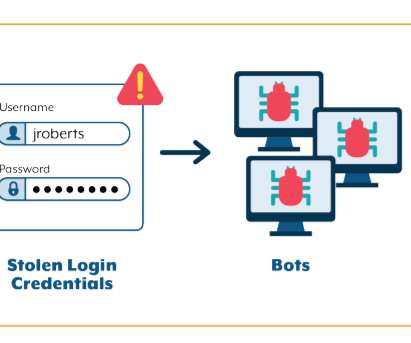
Passkeys and The Beginning of Stronger Authentication madhav Fri, 02/02/2024 - 05:23 How passkeys are rewriting the current threat landscape Lillian, an experienced CISO, surveyed the threat landscape. Despite solid cybersecurity defenses within her enterprise, the reliance on age-old passwords left it vulnerable.















































Let's personalize your content