FBI, Dutch Police Disrupt ‘Manipulaters’ Phishing Gang
Krebs on Security
JANUARY 31, 2025
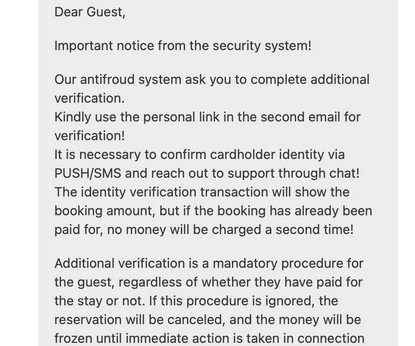
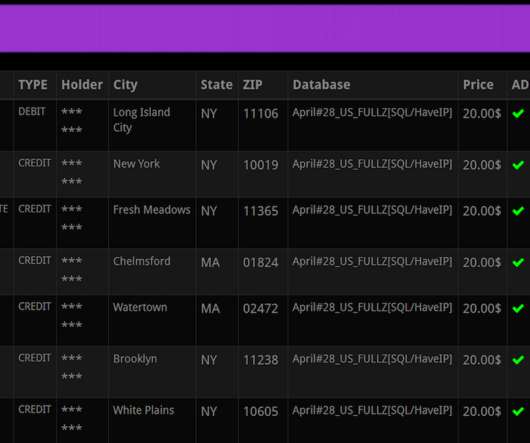
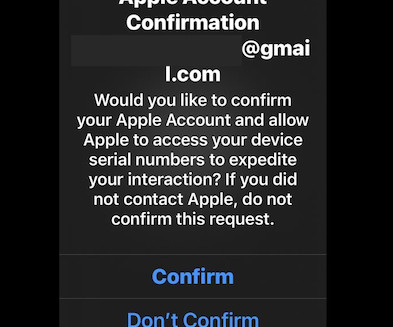
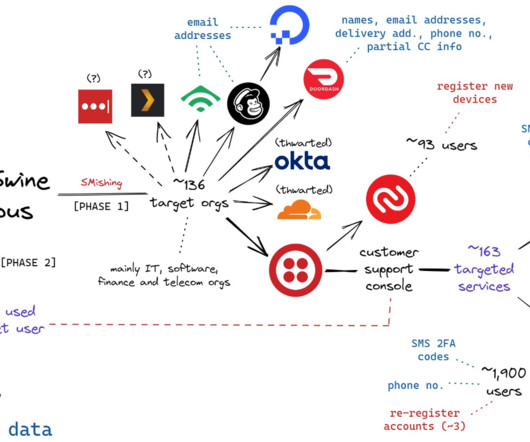
On January 29, the FBI and the Dutch national police seized the technical infrastructure for a cybercrime service marketed under the brands Heartsender , Fudpage and Fudtools (and many other “fud” variations). “The Cybercrime Team is on the trail of a number of buyers of the tools,” the Dutch national police said.











































Let's personalize your content