DDoS amplify attack targets Citrix Application Delivery Controllers (ADC)
Security Affairs
DECEMBER 24, 2020
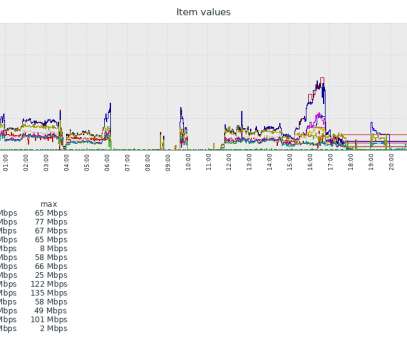
Citrix confirmed that a DDoS attack is targeting Citrix Application Delivery Controller (ADC) networking equipment. Anyone seen UDP reflect DDoS attacks on #citrix #netscaler lately?? It seems a worldwide UDP:443 (EDT) DDOS attack against #NetScaler #gateway is active since last night. SecurityAffairs – hacking, DDoS).
















Let's personalize your content