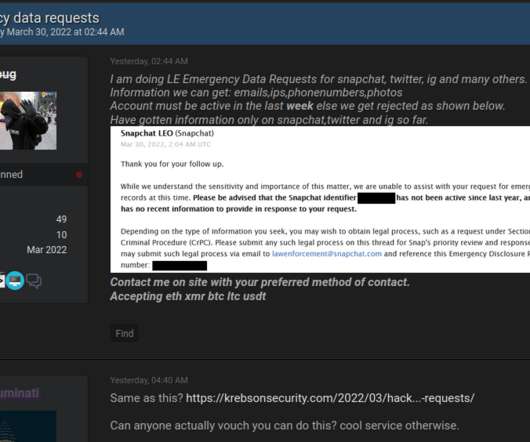
Fake Emergency Search Warrants Draw Scrutiny from Capitol Hill
Krebs on Security
MARCH 31, 2022
The Digital Authenticity for Court Orders Act would require federal, state and tribal courts to use a digital signature for orders authorizing surveillance, domain seizures and removal of online content.










Let's personalize your content