Raspberry Robin operators are selling initial access to compromised enterprise networks to ransomware gangs
Security Affairs
OCTOBER 27, 2022
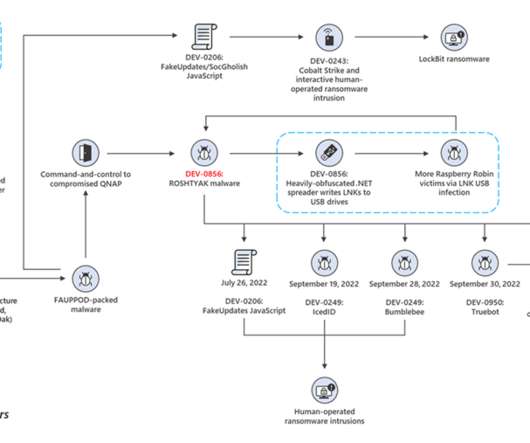
DEV-0950 group used Clop ransomware to encrypt the network of organizations previously infected with the Raspberry Robin worm. Microsoft has discovered recent activity that links the Raspberry Robin worm to human-operated ransomware attacks. . The final-stage malware was the Clop ransomware. ” concludes the report.






















Let's personalize your content