Why SMBs are Under Attack by Ransomware
Webroot
APRIL 13, 2021
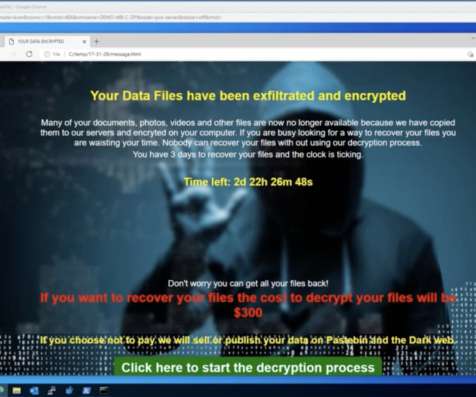
Ransomware attacks generate big headlines when the targets are government entities, universities and healthcare organizations. But there’s one increasingly frequent target of ransomware attacks that tends to slip under the radar. This includes essential security measures like firewalls, endpoint protection and DNS protection.



























Let's personalize your content