Every day is cyber security awareness month
Javvad Malik
OCTOBER 6, 2021
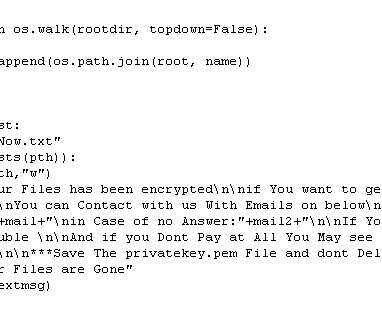
October is National Cyber Security Awareness Month. . Delivering effective cyber security awareness is an ongoing process, and not one that can be solved in one month a year. Operating systems, browsers, security software, and apps, like cats, need to be kept up to date and ‘fed’ the latest updates and patches.









































Let's personalize your content