MyBook Users Urged to Unplug Devices from Internet
Krebs on Security
JUNE 25, 2021
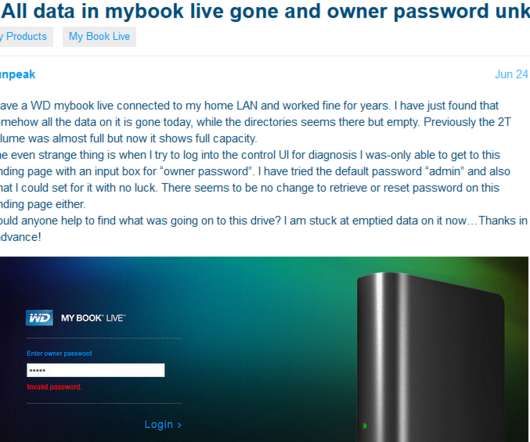
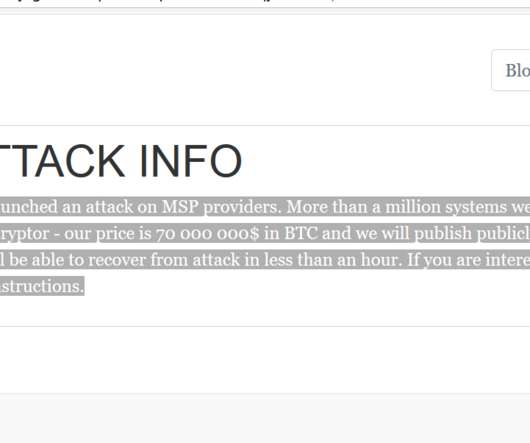
The NVD’s advisory credits VPN reviewer Wizcase.com with reporting the bug to Western Digital three years ago, back in June 2018. That response also suggested this bug has been present in its devices for at least a decade. Examine the CVE attached to this flaw and you’ll notice it was issued in 2018.



















Let's personalize your content