Why Data Protection is Critical to the New U.S. Cybersecurity Strategy
Security Boulevard
APRIL 13, 2023
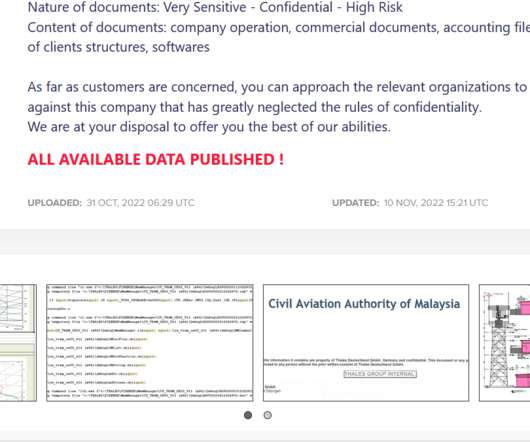
One is the relative agility of threat actors versus those tasked with defending networks and tackling cybercrime. The post Why Data Protection is Critical to the New U.S. Cybersecurity Strategy appeared first on Security Boulevard. Another is the apparent inefficacy of market forces at improving baseline security.






















Let's personalize your content