How the new Spirion-Thales partnership enables sensitive-data-centric encryption
Thales Cloud Protection & Licensing
JUNE 29, 2022
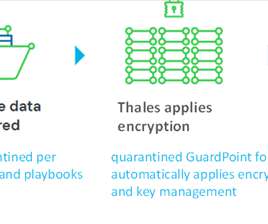
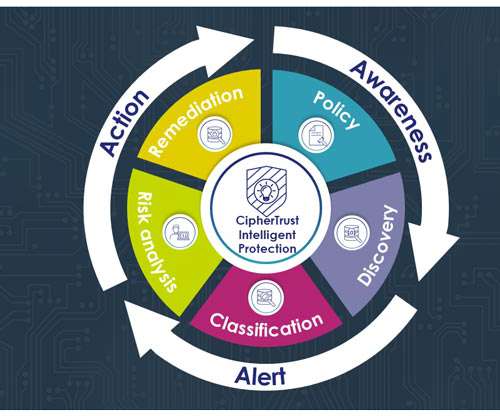
How the new Spirion-Thales partnership enables sensitive-data-centric encryption. To meet the challenges of modern perimeterless, data-driven enterprises, it’s no longer enough to lock down the network. The security must be embedded with the data wherever it travels. Thales CipherTrust Transparent Encryption.



















Let's personalize your content