Hyundai Uses Example Keys for Encryption System
Schneier on Security
AUGUST 22, 2022
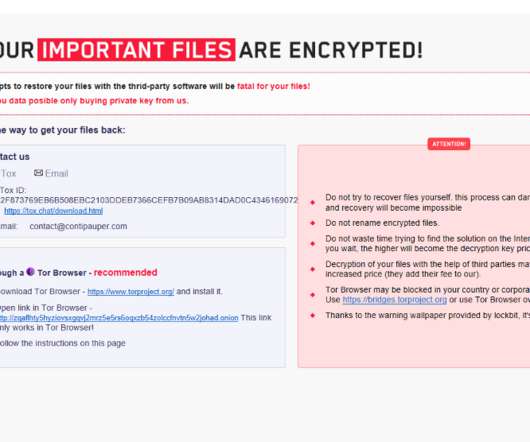
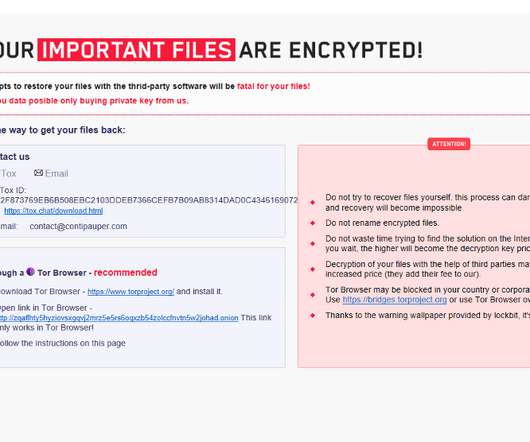
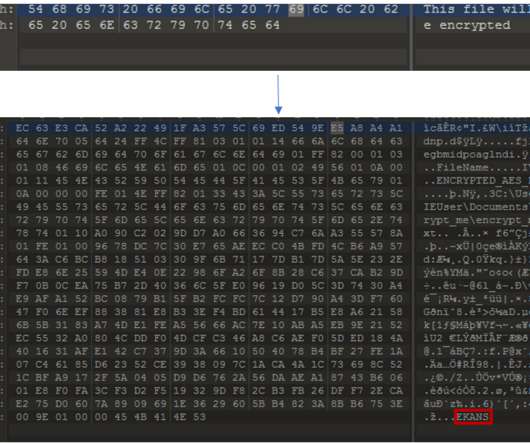
“Turns out the [AES] encryption key in that script is the first AES 128-bit CBC example key listed in the NIST document SP800-38A [PDF]” […]. The search results pointed to a common public key that shows up in online tutorials like “ RSA Encryption & Decryption Example with OpenSSL in C.







































Let's personalize your content