Report Finds Over 50% of Security Practitioners Are Unhappy With Current SIEM Vendor
CyberSecurity Insiders
SEPTEMBER 11, 2021
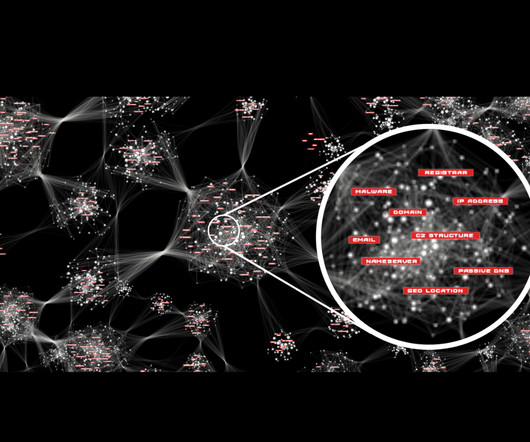
Security industry blogs, magazines, and websites frequently report that many security teams are frustrated by the limitations of their SIEM tool. Analysts find dealing with data collected from numerous hosts within an enterprise to be a daunting task. In that case, additional risk must be assumed by the organization.



















Let's personalize your content