The Clock To Q-Day Is Ticking: InfoSec Global and Thales Provide Collaborative Path to Quantum Readiness
Thales Cloud Protection & Licensing
FEBRUARY 19, 2024
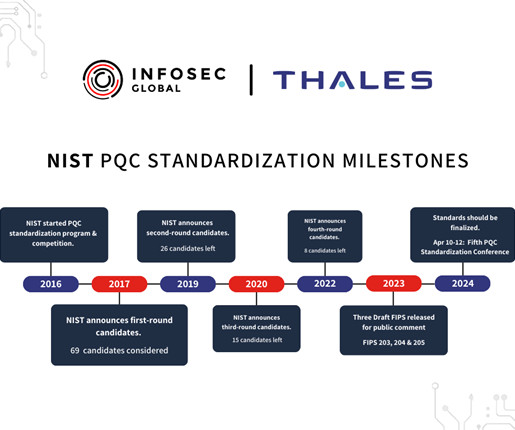
Even before quantum computers possess this compromising capability, adversaries have initiated Harvest Now, Decrypt Later (HNDL) attacks, seizing potentially sensitive data for future adversarial decryption. This vulnerability could expose sensitive enterprise information to risk. In the U.S.,























Let's personalize your content