Accelerate XDR Outcomes with NDR and EDR
Cisco Security
JANUARY 9, 2023
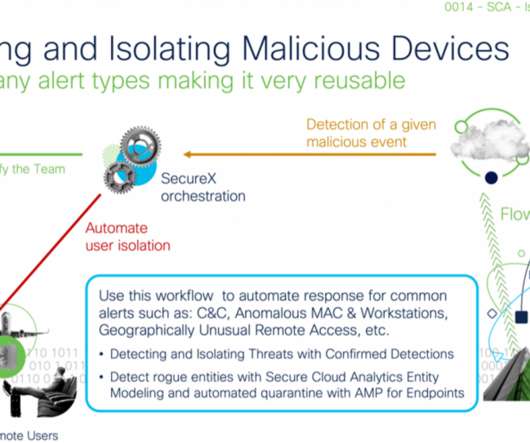
Achieving his tasks accurately is tightly coupled with his ability to scope and understand the impact of an incident and to gather all possible data from the environment which can be associated with an incident including devices, users, files hashes, email ids, domains IPs and others. Automating responses.













Let's personalize your content