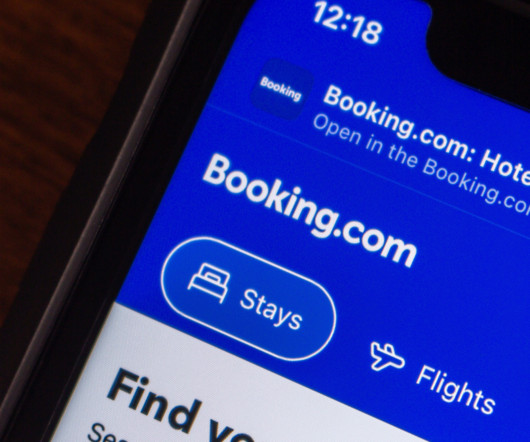
Fake Booking.com phish uses fake CAPTCHAs to trick hotel staff into downloading malware
Malwarebytes
MARCH 26, 2025
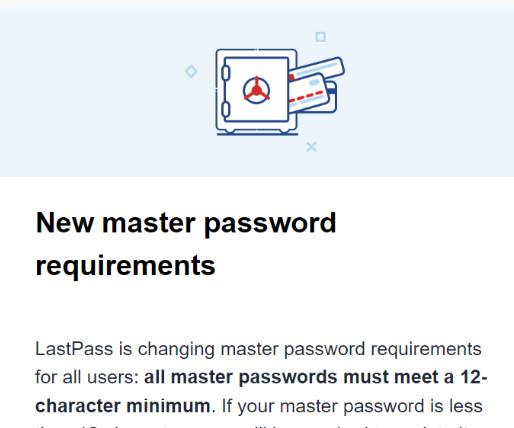
Here’s how it works: Cybercriminals send a fake Booking.com email to a hotels email address, asking them to confirm a booking. Dear Team, You have received a new booking. Use a different password for every online account. Choose a strong password that you dont use for anything else.








































Let's personalize your content