News alert: Sweet Security releases its evolutionary Cloud Native Detection and Response platform
The Last Watchdog
DECEMBER 3, 2024
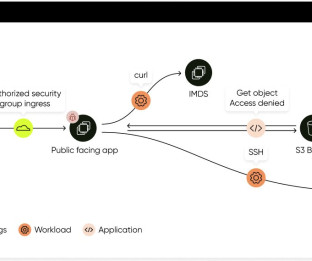
Book a meeting with Sweet Security at AWS re:Invent 2024 in Las Vegas here. About Sweet Security : Specializing in Cloud Native Detection & Response (D&R), Sweet Security protects cloud environments in real time. For too long we’ve been content with mediocre visibility into our most important assets.





























Let's personalize your content