Who’s Behind the DomainNetworks Snail Mail Scam?
Krebs on Security
JULY 3, 2023
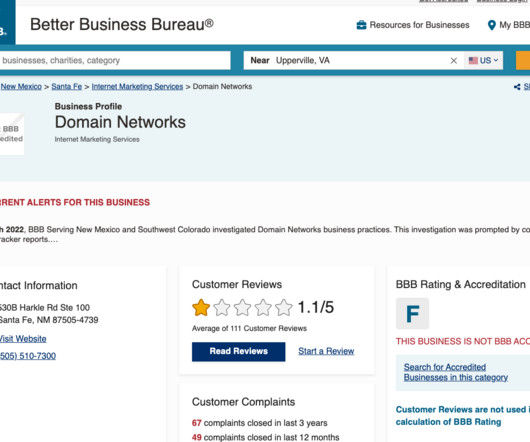
com says it is a business with a post office box in Hendersonville, N.C., There are a few random, non-technology businesses tied to the phone number listed for the Hendersonville address, and the New Mexico address was used by several no-name web hosting companies. The website Domainnetworks[.]com and Renton, Wash.

















Let's personalize your content