The Necessity of Data Security: Recapping the 2019 Thales Data Security Summit
Thales Cloud Protection & Licensing
MAY 14, 2019
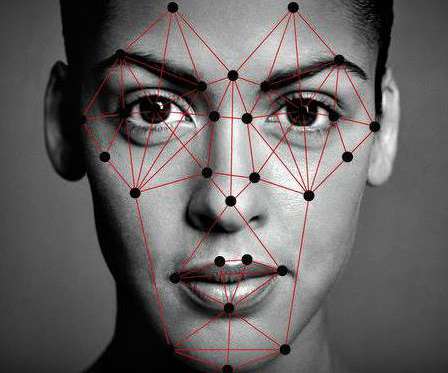
Digital transformation is driving IT modernization, IoT, and cloud migrations at a record pace in the federal government. The ability to narrow the gap between taking advantage of digital transformation without compromising security was a reoccurring theme at our 2019 annual Data Security Summit on May 1.














Let's personalize your content