Why Are We Still Separating Credential Management and Machine Identity Management?
Security Boulevard
MARCH 14, 2022
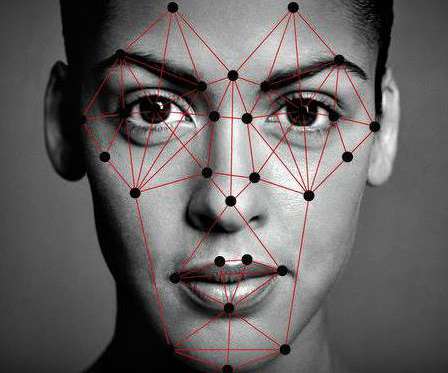
These entities can be tangible, like IoT sensors, mobile devices as well as abstract infrastructures like containers and microservices. Remote work and cloud migration have created new norms and business models. Managing machine identities is equally as important as managing human credentials. Machine Identity Management.










Let's personalize your content