Top 5 Cybersecurity and Computer Threats of 2017
NopSec
FEBRUARY 9, 2017
The year 2016 will be remembered for some big moments in the world of cybersecurity: the largest known distributed denial of service (DDoS) attack, a phishing attack on a United States presidential candidate’s campaign, and ransomware attacks on major healthcare organizations are just a few. Ransomware The U.S.





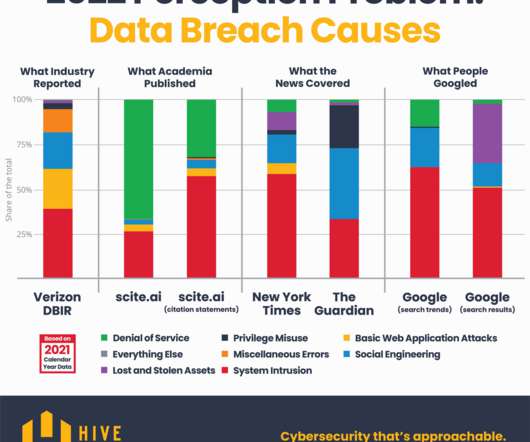
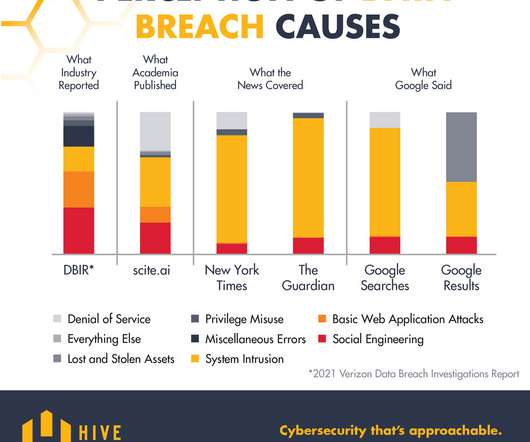

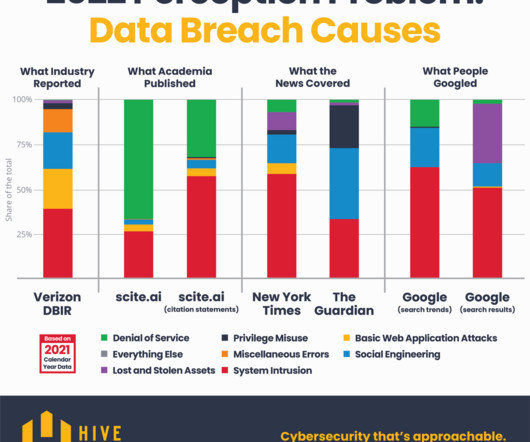






Let's personalize your content