Security expert Marco Ramilli released for free the Malware Hunter tool
Security Affairs
FEBRUARY 6, 2019
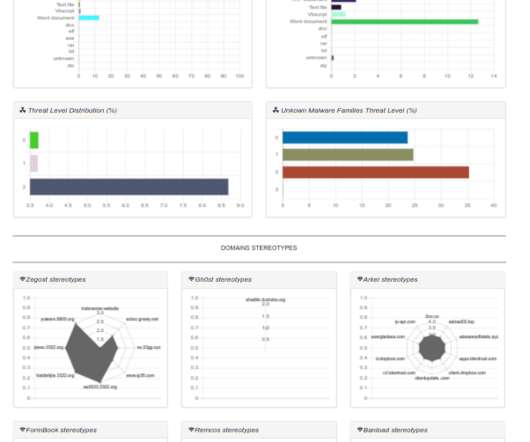
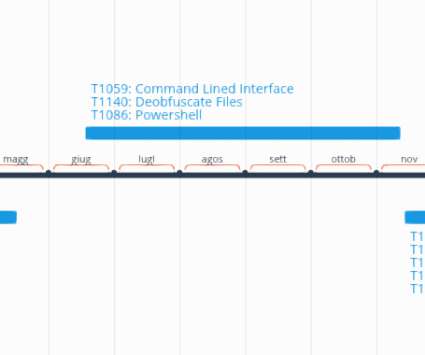
Malware researcher Marco Ramilli released for free the Malware Hunter tool a simple but interesting catching tool base on static YARA rules. Malware researcher Marco Ramilli released for free the Malware Hunter tool a simple but interesting catching tool base on static YARA rules. Malware Static Analysis.



































Let's personalize your content