Cyber Adversary Infrastructure, Explained
Security Boulevard
MAY 24, 2023
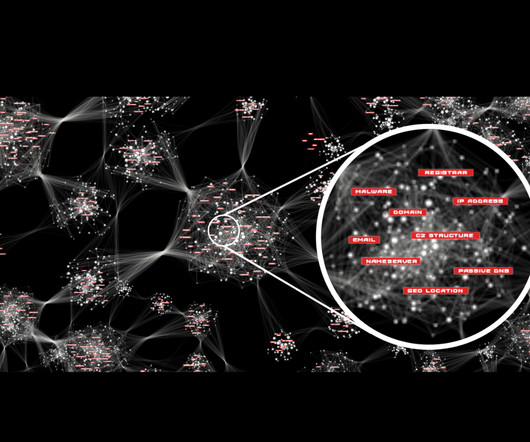
Cyber threat actors rely on infrastructure hidden to most people not looking for it. Revealing such frameworks shines a light on how cyber adversaries operate. Cyber adversary infrastructure is hidden to those who don’t know how to look for it. Data is power. HYAS gives our clients and partners visibility.











Let's personalize your content