Threat Hunting with MITRE ATT&CK
IT Security Guru
OCTOBER 2, 2023
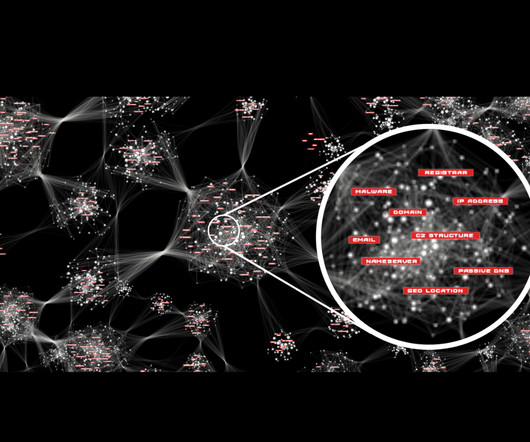
MITRE ATT&CK frameworks ensure you have the correct data sources by telling you which to collect from logs, security systems, and threat intelligence. Automation allows you to save parameters for data collection of the right sources to apply for future hunts.





















Let's personalize your content