CaaS: The Key to More Affordable Cyber Insurance
Security Boulevard
MARCH 20, 2025
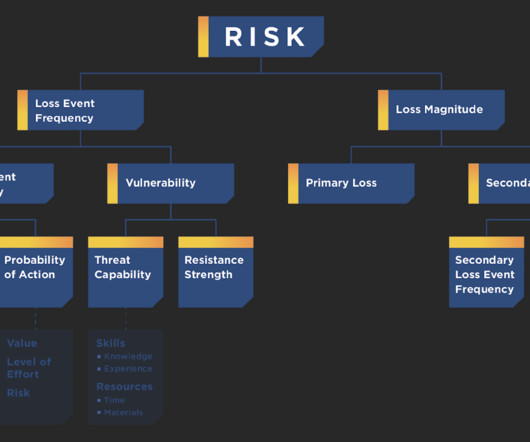
Compliance as a Service (CaaS) strengthens a companys posture and defensibility, making it more attractive to insurers. The post CaaS: The Key to More Affordable Cyber Insurance appeared first on Security Boulevard.



















































Let's personalize your content