Top Cybersecurity Trends to Watch Out For in 2025
Centraleyes
DECEMBER 16, 2024
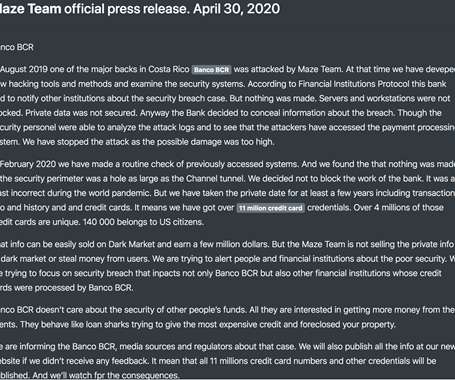
Privacy and Data Protection: A Growing Concern Data privacy will be a growing concern in 2025, especially with increasing scrutiny on how companies collect, store, and share personal information. Expect to see more investments in privacy-enhancing technologies (PETs) such as encryption, anonymization, and data masking.
















































Let's personalize your content