What Is DNS Spoofing and How Is It Prevented?
Security Boulevard
MAY 20, 2022
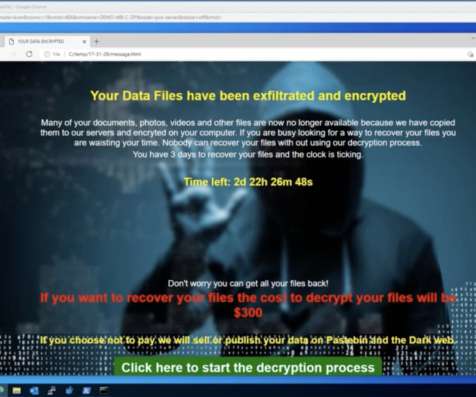
What Is DNS Spoofing and How Is It Prevented? What Is the DNS and DNS Server? . To fully understand DNS spoofing, it’s important to understand DNS and DNS servers. The DNS “domain name system” is then what translates the domain name into the right IP address. What Is DNS Spoofing? .





















Let's personalize your content