TA505 Cybercrime targets system integrator companies
Security Affairs
NOVEMBER 12, 2019
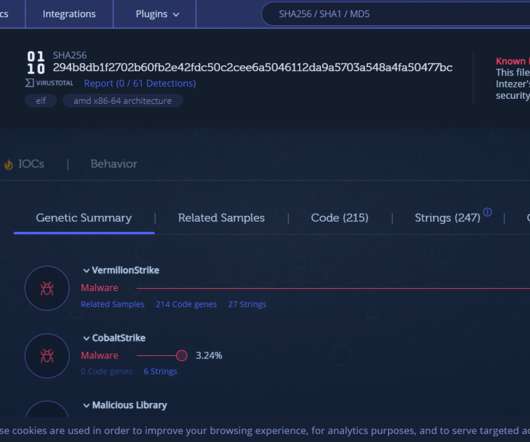
The analysis of a malicious email revealed a possible raising interest of the TA505 cybercrime gang in system integrator companies. Building a re-directors or proxy chains is quite useful for attackers in order to evade Intrusion Prevention Systems and/or protections infrastructures based upon IPs or DNS blocks. Introduction.













Let's personalize your content