Operation Lyrebird: Group-IB assists INTERPOL in identifying suspect behind numerous cybercrimes worldwide
Security Affairs
JULY 6, 2021
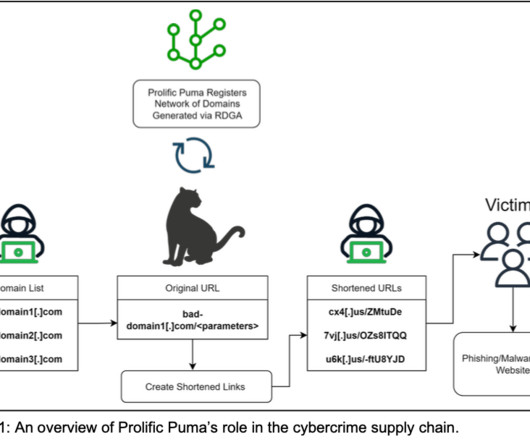
The alleged perpetrator, who turned out to be a citizen of Morocco, was arrested in May by the Moroccan police based on the data about his cybercrimes that was provided by Group-IB. According to the DNS data analysis, this name was used to register at least two domains, which were created using the email from the phishing kit.













Let's personalize your content