Threatening botnets can be created with little code experience, Akamai finds
Tech Republic Security
MAY 31, 2023
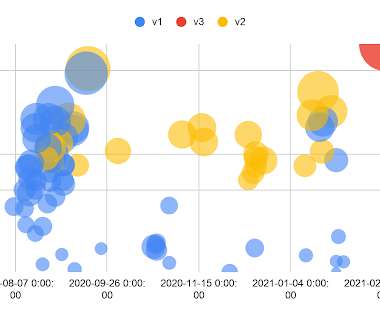
Researchers at Akamai’s Security Intelligence unit find a botnet specimen that reveals how successful DDoS, spam and other cyberattacks can be done with little finesse, knowledge or savvy. The post Threatening botnets can be created with little code experience, Akamai finds appeared first on TechRepublic.



















Let's personalize your content