How to Transition from Security Intelligence to Cybersecurity
CompTIA on Cybersecurity
JULY 22, 2021
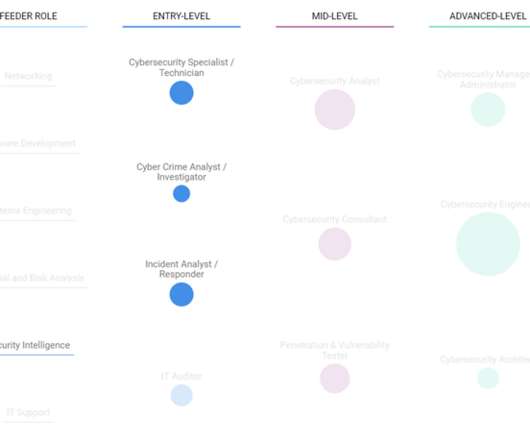
The IT career path from security intelligence to cybersecurity is just one example of a route you can take in the CyberSeek career pathway.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.
CompTIA on Cybersecurity
JULY 22, 2021
The IT career path from security intelligence to cybersecurity is just one example of a route you can take in the CyberSeek career pathway.

SecureBlitz
DECEMBER 15, 2021
This post will show you how to fight phishing with security intelligence. The post How To Fight Phishing With Security Intelligence appeared first on SecureBlitz Cybersecurity. The post How To Fight Phishing With Security Intelligence appeared first on SecureBlitz Cybersecurity.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
NOVEMBER 3, 2023
Permalink The post DEF CON 31 Packet Hacking Village – Mike Raggo’s, Chet Hosmer’s ‘OSINT for Physical Security Intelligence’ appeared first on Security Boulevard. Originating from the conference events at Caesars Forum, Flamingo, Harrah’s and Linq in Las Vegas, Nevada ; via the organizations YouTube channel.
CSO Magazine
NOVEMBER 29, 2021
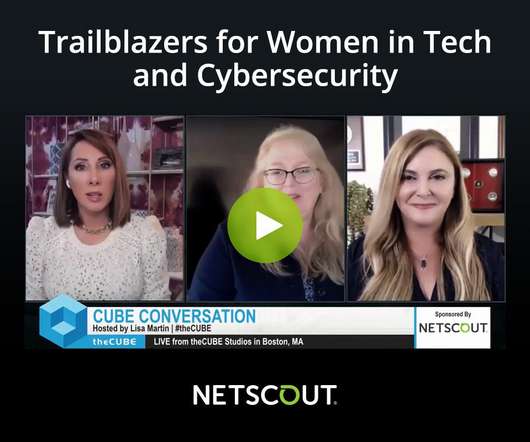
NETSCOUT's Chief Security Officer, Debby Briggs, was joined by Tyler Cohen Wood for an insightful conversation with Lisa Martin from theCUBE. Tyler is a nationally recognized cyber security, intelligence, national security expert, and former Director of Cyber Risk Management for AT&T.

Penetration Testing
APRIL 23, 2024
In a disturbing new development, cybersecurity experts at AhnLab Security Intelligence Center (ASEC) have revealed a growing trend of infostealer malware abusing the Electron framework.

Penetration Testing
JANUARY 30, 2024
In a concerning development in the realm of cybersecurity, the Akamai Security Intelligence Response Team (SIRT) has uncovered a series of critical vulnerabilities in various Hitron DVR models.

Penetration Testing
MAY 1, 2024
The world of cybersecurity is witnessing an alarming trend as ransomware groups intensify their attacks on Microsoft SQL (MS-SQL) servers, exploiting weak management practices to deploy devastating malware.

Penetration Testing
FEBRUARY 2, 2024
In the shadowy corners of the internet, an unending battle rages between cybersecurity defenders and nefarious cybercriminals.

Tech Republic Security
MAY 31, 2023
Researchers at Akamai’s Security Intelligence unit find a botnet specimen that reveals how successful DDoS, spam and other cyberattacks can be done with little finesse, knowledge or savvy. The post Threatening botnets can be created with little code experience, Akamai finds appeared first on TechRepublic.

CSO Magazine
JUNE 8, 2023
IT infrastructure services provider Kyndryl has announced a new cybersecurity incident response and forensics (CSIRF) service as well as a new threat intelligence collaboration with AWS.

Tech Republic Security
AUGUST 18, 2017
In volume 22 of Microsoft's Security Intelligence Report, the Redmond giant outlined some of the biggest cyberthreats facing its users.

Webroot
DECEMBER 14, 2020
The cybersecurity industry and end-of-year predictions go together like Fall and football or champagne and the New Year. One thing the cybersecurity experts at Webroot agree on is that work from home is here to stay for 2021, or at least it won’t recede to pre-pandemic levels in even the medium-term.

Security Affairs
MAY 18, 2022
pic.twitter.com/Tro0NfMD0j — Microsoft Security Intelligence (@MsftSecIntel) May 17, 2022. pic.twitter.com/stXJMDMevc — Microsoft Security Intelligence (@MsftSecIntel) May 17, 2022. — Microsoft Security Intelligence (@MsftSecIntel) May 17, 2022.

CyberSecurity Insiders
MAY 20, 2021
Thus, customers can avail of the service to simplify the operations related to security intelligence across their teams, tools, and partners. . The post AI company Splunk to acquire cloud-based threat intelligence firm TruSTAR appeared first on Cybersecurity Insiders.

CSO Magazine
APRIL 19, 2023
The great power competition is alive and well and is the constant theme throughout the various assessments.
Security Boulevard
FEBRUARY 25, 2022
Palo Alto Networks this week launched a cybersecurity platform that was developed from the ground up to take advantage of advances in artificial intelligence (AI).

Security Boulevard
MARCH 8, 2023
Palo Alto Networks this week revealed it added a threat detection and response module to its Cortex extended security intelligence and automation management (XSIAM) platform that uses machine learning algorithms to surface anomalous activity based on identity and user behavior.

CyberSecurity Insiders
JUNE 18, 2021
Recorded Future that offers Enterprise Security Intelligence to American companies has revealed that there has been a persistent cyber threat to Indian Defense and Telecom sector from Chinese Military Intelligence since 2014.

Krebs on Security
SEPTEMBER 24, 2020
Department of Homeland Security issued an emergency directive instructing all federal agencies to patch the vulnerability by Sept. Last night, Microsoft’s Security Intelligence unit tweeted that the company is “tracking threat actor activity using exploits for the CVE-2020-1472 Netlogon vulnerability.”

Security Affairs
MAY 15, 2022
Microsoft Security Intelligence team Microsoft reported that a new variant of the Sysrv botnet, tracked as Sysrv-K, now includes exploits for vulnerabilities in the Spring Framework and WordPress. — Microsoft Security Intelligence (@MsftSecIntel) May 13, 2022.

Security Boulevard
APRIL 19, 2021
In the last 30 days, education was the most targeted sector, receiving more than 60% of all malware encounters, or more than 5 million incidents, according to Microsoft Security Intelligence. The post Online Ed is the New Corporate Threat Vector appeared first on Security Boulevard. Department of.

Heimadal Security
OCTOBER 4, 2022
The Finnish Security Intelligence Service (SUPO) warns of a highly likely intensification of cyberespionage activities conducted by Russia-linked threat actors over the winter.

Malwarebytes
AUGUST 16, 2021
Synology NAS devices are under attack from StealthWorker PrintNightmare and RDP RCE among major issues tackled by Patch Tuesday Thief pulls off colossal, $600m crypto-robbery…and gives the money back If a QR code leads you to a Bitcoin ATM at a gas station, it’s a scam Twitter says it out loud: removing anonymity will not stop online abuse Microsoft’s (..)
Hot for Security
MARCH 12, 2021
Microsoft’s Security Intelligence account also tweeted , “We have detected and are now blocking a new family of ransomware being used after an initial compromise of unpatched on-premises Exchange Servers.”. “Microsoft observed a new family of human operated ransomware attack customers – detected as Ransom:Win32/DoejoCrypt.A.
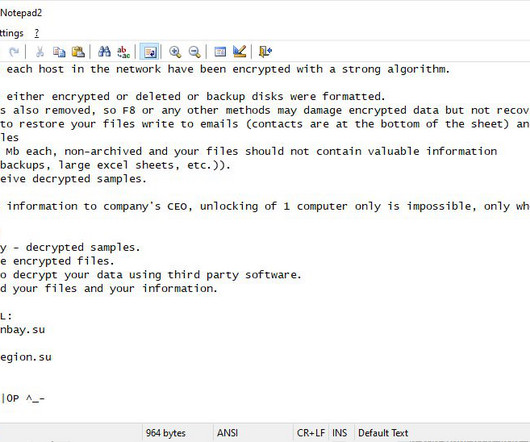
Security Affairs
MAY 20, 2023
Researchers at Microsoft Security Intelligence team published a series of tweets to warn of a new wave of attacks aimed at distributing the Clop ransomware and linked it to the financially motivated cybercriminal group Sangria Tempest (ELBRUS, FIN7 ). ” reads one of the tweets published by the experts. We are in the final!

Daniel Miessler
NOVEMBER 6, 2020
I think there are four main trends that will play out in the field of information security in the next 20 years. 2026-) Cyberinsurance will ascend as the primary mechanism for making cybersecurity-related product and service decisions within companies. ISC) 2 says there were over 4 million too few cybersecurity people in 2019.

Heimadal Security
FEBRUARY 15, 2023
Its Security Intelligence team is tracking the cluster under the emerging name DEV-0147. Chinese adversarial collectives with links to the Ministry […] The post Chinese Hackers Use ShadowPad Against South American Diplomatic Entities appeared first on Heimdal Security Blog.
CompTIA on Cybersecurity
NOVEMBER 5, 2021
If you have a background in security intelligence and understand the cloud, a specialization as a cloud penetration tester may be a good next step for you.
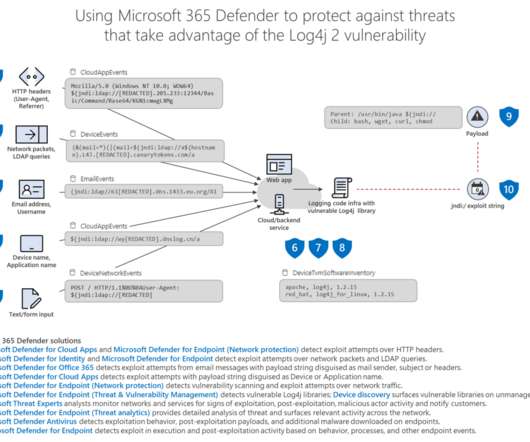
Security Affairs
JANUARY 11, 2022
link] — Microsoft Security Intelligence (@MsftSecIntel) January 11, 2022. According to Microsoft Night Sky ransomware operators employed C2 servers that impersonate domains used by legitimate companies such as cybersecurity firms Trend Micro, Sophos, and IT firms such as Nvidia and Rogers Corporation. trendmrcio[.]com,

Security Boulevard
APRIL 25, 2022
today launched a cloud-based platform through which it will unify risk and threat assessments using data collected from both its own and third-party security offerings. The post Trend Micro Unfurls Risk Intel Aggregator appeared first on Security Boulevard. Trend Micro Inc.

CyberSecurity Insiders
OCTOBER 3, 2022
Monitoring and tracking potential threats from the dark web, open source, and social media platforms to detect threats that could attack your organization is critical to ensure public and corporate safety and security. The Nisos team will prepare the client’s finished intelligence product and review their findings and recommendations.

Webroot
JUNE 25, 2021
The conversation covers the issues of IoT and home network security both from the perspective of the average family household and what the age of remote work means for employees working on their own networks. Security intelligence director Grayson Milbourne brings a unique perspective to the podcast.
Security Affairs
MAY 20, 2021
Microsoft Security Intelligence researchers uncovered a malware campaign that is spreading a remote access trojan (RAT) tracked as STRRAT. pic.twitter.com/mGow2sJupN — Microsoft Security Intelligence (@MsftSecIntel) May 19, 2021.
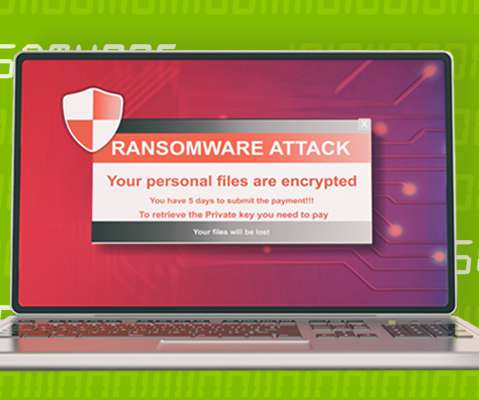
Webroot
NOVEMBER 5, 2021
explains Grayson Milbourne, security intelligence director for Carbonite + Webroot. Cybersecurity experts are developing new tools for keeping cybercriminals out of your business and personal life. Ransomware tactics. Their goal is disruption. How can your business operate if all the computers are locked up?” How to fight back.

Spinone
NOVEMBER 6, 2017
Artificial Intelligence: The White Side The White House has published a press release as well as a report on Artificial Intelligence, specifically highlighting the Administrations’ plans with AI, how it will handle cybersecurity , and what impact it will have on the economy and the workforce in the US.

CyberSecurity Insiders
AUGUST 27, 2022
Nisos provides the people, processes, and technologies necessary to deliver actionable intelligence as a managed service. Executive protection offerings today are focused primarily on cybersecurity. They typically neglect intelligence about physical and reputational threats. Nisos is The Managed Intelligence Company.

Webroot
OCTOBER 13, 2021
Ransomware attacks dominate news coverage of the cybersecurity industry. The first types of ransomware have existed for quite some time, going all the way back to the early 2000’s,” says Grayson Milbourne, security intelligence director at Carbonite + Webroot. “The The Rise of Ransomware. Evolving Threats.

SC Magazine
APRIL 12, 2021
Managing cybersecurity for an organization today requires a lot of skill and patience. But we’re not here to harp on the problem – we want to propose a solution: Using security intelligence to enable risk-prioritized vulnerability management. Prioritize through a risk and security intelligence lens.
Security Affairs
APRIL 30, 2020
— Microsoft Security Intelligence (@MsftSecIntel) April 28, 2020. ” reads the Tweet published by the Microsoft Security Intelligence team. . ” reads the Tweet published by the Microsoft Security Intelligence team. — Microsoft Security Intelligence (@MsftSecIntel) April 28, 2020.
Security Affairs
MAY 4, 2020
pic.twitter.com/EbI8kxICQG — Microsoft Security Intelligence (@MsftSecIntel) May 4, 2020. The attachment is a ZIP archive containing the familiar ISO file carrying a malicious SCR file with misleading icon pic.twitter.com/o1FbMUbTBs — Microsoft Security Intelligence (@MsftSecIntel) May 4, 2020.

Security Affairs
OCTOBER 6, 2020
The Cybersecurity and Infrastructure Security Agency (CISA) issued an alert to warn of a surge of Emotet attacks that have targeted multiple state and local governments in the U.S. In mid-September, cybersecurity agencies across Asia and Europe warned of Emotet spam campaigns targeting businesses in France, Japan, and New Zealand.

Malwarebytes
JULY 5, 2021
Other cybersecurity news. Stay safe, everyone!

CyberSecurity Insiders
DECEMBER 18, 2021
By cybersecurity expert and J2 CEO John Mc Loughlin. Companies deploy multiple security, intelligence and productivity monitoring tools in the hopes of working smarter and safer. The post The Greatest Asset Becomes the Biggest Risk appeared first on Cybersecurity Insiders.

Webroot
JUNE 2, 2022
MDR services offer threat detection and response capabilities by augmenting cybersecurity tools with human security intelligence. Leveraging this human security expertise, MDR integrates, synthesizes and contextualizes security and other event information to hunt for, understand and respond to security incidents.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content