New Report on IoT Security
Schneier on Security
SEPTEMBER 28, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
SEPTEMBER 28, 2022
The Atlantic Council has published a report on securing the Internet of Things: “Security in the Billions: Toward a Multinational Strategy to Better Secure the IoT Ecosystem.”

Schneier on Security
SEPTEMBER 27, 2018
This one is from NIST: " Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks." It's still in draft. Remember, there are many others.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
DECEMBER 16, 2024
Businesses must adopt tools and automation capable of invoking immediate action, even at the risk of false positives. Raising security baselines across industries is essential, with risk mitigationnot acceptancebecoming the standard. Alkove Jim Alkove , CEO, Oleria Identity is cybersecurity’s biggest challenge.

SecureWorld News
JANUARY 8, 2025
Cyber Trust Mark, a voluntary cybersecurity labeling program designed to help consumers make informed decisions about the security of their internet-connected devices. From baby monitors to home security systems, these IoT products have become integral to daily life, yet they also present significant cybersecurity risks.

Security Affairs
JANUARY 4, 2025
Treasury Department sanctioned Chinese cybersecurity firm Integrity Tech for its involvement in attacks attributed to the Flax Typhoon group. Treasury sanctioned a Chinese cybersecurity firm, Integrity Tech, for links to cyberattacks by Chinas state-backed Flax Typhoon APT group (also called Ethereal Panda or RedJuliett).

SecureWorld News
NOVEMBER 7, 2024
The journey from sensors in the field to servers in the control room is a cybersecurity tightrope journey. A single mistake can pose a significant risk to infrastructure and to the public. But the moment we bring IoT into the mix, we create thousands of potential entry points for attackers.

Schneier on Security
NOVEMBER 13, 2018
But like nearly all innovation, there are risks involved. And for products borne out of the Internet of Things, this means the risk of having personal information stolen or devices being overtaken and controlled remotely. But it's just one of dozens of awful "security" measures commonly found in IoT devices.

SecureWorld News
MAY 2, 2025
Healthcare cybersecurity is undergoing explosive growth, reflecting both escalating threats and urgent investments to protect patient data and systems. According to a new report, the global healthcare cybersecurity market was valued at US $21.25 billion in 2024 and is projected to reach $82.90 billion by 2033, at a robust 18.55% CAGR.

The Last Watchdog
NOVEMBER 9, 2020
The Internet of Things (IoT) has come a long, long way since precocious students at Carnegie Melon University installed micro-switches inside of a Coca-Cola vending machine so they could remotely check on the temperature and availability of their favorite beverages. Related: Companies sustain damage from IoT attacks That was back in 1982.

Joseph Steinberg
NOVEMBER 17, 2021
Rockville, MD – November 17, 2021 – Sepio Systems , the leader in Zero Trust Hardware Access (ZTHA), announced today that cybersecurity expert Joseph Steinberg has joined its advisory board. Steinberg has led organizations within the cybersecurity industry for nearly 25 years and is a top industry influencer worldwide.

Tech Republic Security
DECEMBER 20, 2022
A new Comcast study hints at a major risk to businesses, governments and public systems due to poor cybersecurity in the booming Internet of Things industry. The post Study: Consumer security savvy is way behind IoT threat landscape appeared first on TechRepublic.

Centraleyes
DECEMBER 16, 2024
As we approach 2025, the cybersecurity landscape is evolving rapidly, shaped by technological advancements, regulatory shifts, and emerging threats. Below is an exhaustive list of key cybersecurity trends to watch out for in 2025. Lets explore the top current cybersecurity trends this year. The challenge?
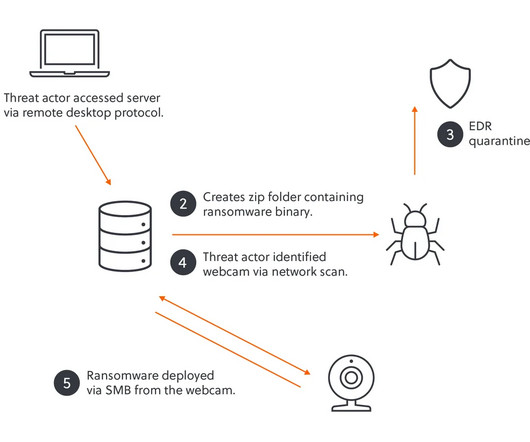
Security Affairs
MARCH 8, 2025
Cybersecurity researchers at S-RM team discovered a novel attack technique used by the Akira ransomware gang. They found unsecured IoT devices, including webcams and a fingerprint scanner, using them to bypass security defenses and successfully deploy the ransomware. ” reads the report published by the S-RM team.

SecureWorld News
FEBRUARY 17, 2025
Cybersecurity governance has undergone a dramatic transformation over the past few decades. We have moved beyond traditional compliance-driven security models to risk-based approaches, integrating cybersecurity into enterprise risk management (ERM) frameworks. But the question remains: where are we headed?

The Last Watchdog
MARCH 25, 2025
FinTech and Communications Leader, IDT Corporation partners with AccuKnox to deploy runtime security-powered CNAPP (Cloud Native Application Protection Platform) for IoT/Edge Security. This proactive approach aims to mitigate risks associated with AI-driven operations. Menlo Park, Calif., 25, 2025, CyberNewswire — AccuKnox, Inc.

SecureWorld News
JANUARY 23, 2025
Industrial automation and operational technology (OT) are at a critical intersection where cybersecurity is not a "nice to have" but an essential component of system design and implementation. On the other hand, many believe that a foundational understanding of controls engineering is essential to being a competent OT cybersecurity engineer.

Security Boulevard
MARCH 21, 2025
Check out key findings and insights from the Tenable Cloud AI Risk Report 2025. And get the latest on open source software security; cyber scams; and IoT security. 1 - Tenable: Orgs using AI in the cloud face thorny cyber risks Using AI tools in cloud environments?

Joseph Steinberg
APRIL 7, 2021
Today, however, after, having had literally hundreds of conversations with, and about, Israeli cybersecurity companies, I thought that I would mention to my readers a few of the firms that I find interesting. The firm has also expanded into cybersecurity systems for aircraft. Argus Cyber Security . Axis Security.

Security Boulevard
JANUARY 8, 2025
The post Insecure Medical Devices Illumina DNA Sequencer Illuminates Risks appeared first on Security Boulevard. IEI-IEI, Oh: Running an obsolete OS, on obsolete hardware, configured with obsolete settings.

SecureWorld News
JUNE 13, 2023
In a digital landscape increasingly dependent on interconnected devices, the rise in malicious Internet of Things (IoT) botnet activity is becoming a significant cause for concern. This tactic is commonly associated with a variety of IoT botnets, exploiting the lax security measures present in billions of IoT devices worldwide.

Security Boulevard
JUNE 15, 2025
We discuss the inherent vulnerabilities that come with these advancements, including cybersecurity threats and real-life incidents such as hacked crosswalk signals featuring voices of tech moguls. The Cybersecurity Risks of Smart Cities appeared first on Shared Security Podcast.

Hacker's King
DECEMBER 24, 2024
As the digital landscape evolves, cybersecurity remains a critical concern for businesses, governments, and individuals alike. With the advent of new technologies and rising cyber threats , 2025 promises significant shifts in the cybersecurity domain. YOU MAY ALSO WANT TO READ ABOUT: Can Cybersecurity Make You a Millionaire?

SecureWorld News
APRIL 13, 2025
In this article, we'll explore how AI enhances cybersecurity, its key benefits, and why businesses are increasingly relying on AI-driven security solutions. How does AI work in cybersecurity? It helps identify anomalies and potential third-party risks in real-time.

SecureWorld News
JANUARY 16, 2025
This article delves deeper into the challenges faced by the oil and gas industry, highlighting practical strategies to safeguard critical infrastructure through cybersecurity, data analytics, and regulatory compliance. Regularly updating and patching systems, including antivirus software, firewalls, and SCADA networks, can mitigate this risk.

SecureWorld News
FEBRUARY 5, 2025
The State of Cybersecurity in Canada 2025 report, published by the Canadian Cybersecurity Network (CCN) and the Security Architecture Podcast , delivers an in-depth analysis of the evolving threat landscape, emerging risks, and strategic recommendations for Canadian organizations.

SecureWorld News
OCTOBER 16, 2024
The flaw has exposed the widely distributed smart vacuums to manipulation by bad actors, raising concerns about the cybersecurity of internet-connected home devices. Back in 2017, SecureWorld News reported that cybersecurity researchers took control of an LG 'Smart' vacuum and spied on the home through the device's camera.

Trend Micro
MARCH 30, 2023
In this fourth article, I introduce the discussion related to Industrial IoT, that is involved challenges to adopt cybersecurity strategy into modernizing environment.

eSecurity Planet
JANUARY 20, 2022
Incidents of malware targeting Linux-based Internet of Things (IoT) devices jumped by more than a third in 2021, with three malware families the primary drivers behind the increase. Threats to Open Source, IoT. Also read: Top IoT Security Solutions for 2022. IoT devices pose two fundamental threats,” he said.

Tech Republic Security
MARCH 13, 2023
By exploiting webcams and other IoT devices, hackers can spy on private and professional conversations, potentially giving them access to sensitive information, says BitSight. The post How internet-facing webcams could put your organization at risk appeared first on TechRepublic.

Cisco Security
FEBRUARY 6, 2023
The use of unmanaged and IoT devices in enterprises is growing exponentially, and will account for 55.7 A critical concern is deploying IoT devices without requisite security controls. Furthermore, 83% of IoT-based transactions happen over plaintext channels and not SSL, making them especially risky.

SecureWorld News
FEBRUARY 20, 2025
The FBI, CISA, and MS-ISAC have issued a joint cybersecurity advisory warning organizations about Ghost (Cring) ransomware, a sophisticated cyber threat that has been compromising critical infrastructure, businesses, and government entities worldwide. Stolen credentials remain the top breach factor, responsible for 24% of incidents in 2024.

SecureWorld News
SEPTEMBER 19, 2024
This division of function, however, and both logical and physical separation is blurring as IoT rises to connect more and more discrete systems, while IT and OT are increasingly forced to work together to modernize industry and critical infrastructure, to help mechanical systems to become "smart."

SecureWorld News
JUNE 18, 2025
When renewable energy becomes a security risk Some people are concerned about whether solar panels will operate after periods of cloudy weather, others are more concerned about whether they can be remotely accessed. We know IoT can be insecure. In fact, years ago I gave a talk on the IoT insecurities, and it's still true today.

SecureWorld News
JULY 22, 2024
On July 17, cybersecurity experts gathered at Cecil College for the Cybersecurity in Agriculture Forum to discuss the escalating threats to digital information and privacy across all sectors, specifically agriculture. Everybody in the ag field should be thinking about cybersecurity," Fitzgerald added.

Security Boulevard
FEBRUARY 9, 2023
Implementing modern cryptography standards on tiny IoT devices is hard. The post Amazing Fast Crypto for IoT — US NIST Fingers ASCON appeared first on Security Boulevard. They’re underpowered, need to sip battery charge and something like AES is often overkill.

Security Boulevard
MARCH 31, 2025
In this blog, we share three challenges cybersecurity leaders say exposure management helps them solve. The core cybersecurity discipline is evolving into exposure management , which is built on a broader, more strategic approach to identifying, prioritizing and mitigating risk. We have to shift to a risk approach."

SecureWorld News
MAY 19, 2025
Currently in orbit around Earth are more than 12,000 active satellites, forming a vast web of data pipelines, IoT devices, and AI-driven ground stations that rivals any terrestrial datacenter in complexity and density. Forget spaceship battles and photon torpedoesthe real battle among the stars is cyber.

Security Boulevard
MARCH 21, 2024
IoT producers must comprehend the relevant rules, consult legal and technological experts and evaluate cybersecurity procedures. The post IoT Consumer Labeling Goes Global – What This Means for Vendors and Consumers appeared first on Security Boulevard.

SecureWorld News
OCTOBER 25, 2023
The global cybersecurity landscape is a minefield, with new threats emerging all the time. One way to mitigate supply chain risk is to implement a global cybersecurity rating system. This would allow businesses to assess the security posture of their suppliers and identify any potential risks.

Security Boulevard
JUNE 2, 2023
The post 5G and Cybersecurity Risks in 2023 appeared first on Security Boulevard. Four years later, the number of people with 5G-enabled devices is still small in most countries. It’s uncertain if the reason behind the sluggish adoption is affordability, the lack of.

Security Boulevard
APRIL 30, 2024
The post Brits Ban Default Passwords — and More IoT Stupidity appeared first on Security Boulevard. The UK’s Product Security and Telecommunications Infrastructure Act aims to improve the security of net-connected consumer gear.

ZoneAlarm
FEBRUARY 23, 2025
Mars Hydro, a Chinese company that makes IoT devices like LED lights and hydroponics equipment, recently suffered a massive data breach, exposing approximately 2.7 This breach has raised serious concerns about the security of internet-connected devices and the potential risks for consumers. billion records.

CyberSecurity Insiders
MAY 12, 2022
Nokia, once renowned for its amazing mobile phones, has now developed a testing lab completely dedicated to cybersecurity in the United States. Simultaneously, it will also act as a threat intelligence sharing platform and will work with the community to identify and mitigate risks associated with cyber-attacks on 5G networks.

Security Boulevard
MARCH 7, 2025
Check out best practices for shoring up data security and reducing cyber risk. 1 - CSA: How to boost data security and reduce cyber risk Risk assessment gaps. 1 - CSA: How to boost data security and reduce cyber risk Risk assessment gaps. Plus, get tips on how to improve job satisfaction among tech staff.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content