Threat Report Portugal Q1 2020
Security Affairs
APRIL 20, 2020
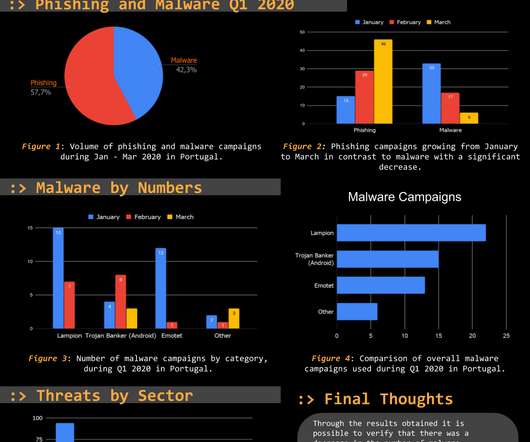
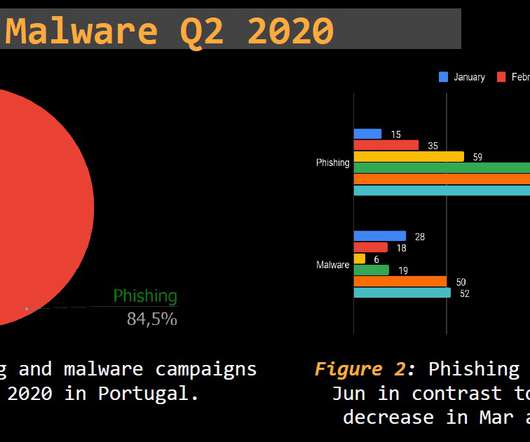
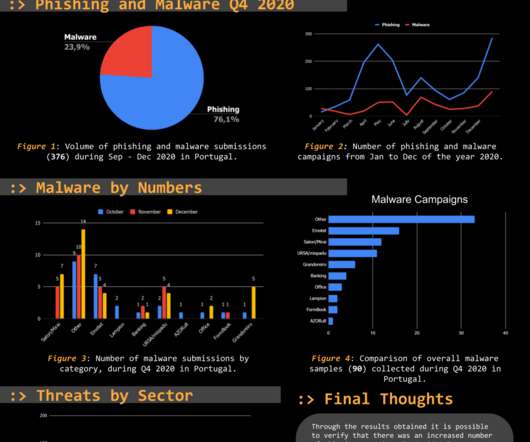
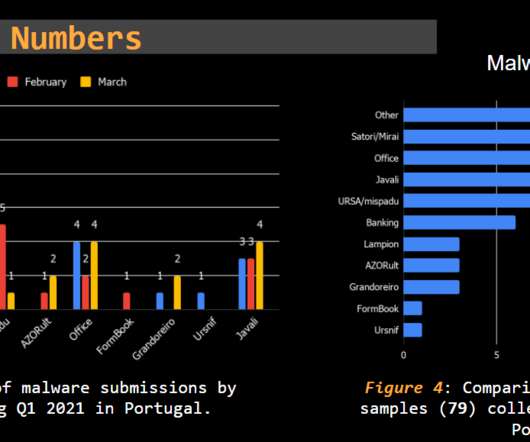
Threat Report Portugal Q1 2020: Phishing and malware by numbers. This makes it a reliable and trustworthy and continuously updated source, focused on the threats targeting Portuguese citizens. This makes it a reliable and trustworthy and continuously updated source, focused on the threats targeting Portuguese citizens.

































Let's personalize your content