How to Address the Requirements of Personal Data Protection (PDP) Law of Indonesia
Thales Cloud Protection & Licensing
FEBRUARY 1, 2023
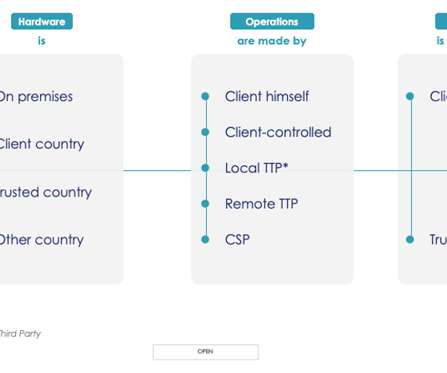
It also introduces new concepts, including the requirement for notifying the regulator of any cross-border personal data transfers (both before and after the transfer). The new law goes further by introducing criminal sanctions for personal data breaches.













Let's personalize your content