Security Affairs newsletter Round 418 by Pierluigi Paganini – International edition
Security Affairs
MAY 6, 2023
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

Security Affairs
MAY 6, 2023
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

Thales Cloud Protection & Licensing
FEBRUARY 1, 2023
It also introduces new concepts, including the requirement for notifying the regulator of any cross-border personal data transfers (both before and after the transfer). The new law goes further by introducing criminal sanctions for personal data breaches.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

eSecurity Planet
MAY 20, 2024
Digital rights management (DRM) is an encryption technology that enforces creator’s rights. Digital rights management wraps digital data into an encrypted wrapper tied to a license that contains the rules for how the content may be used. IP address, geographic location, or device type.

Duo's Security Blog
AUGUST 16, 2021
Enforcing security requirements such as OS updates and disk encryption help organizations set a baseline for healthy and compliant devices. For critical applications and environments with sensitive data (e.g., For critical applications and environments with sensitive data (e.g.,
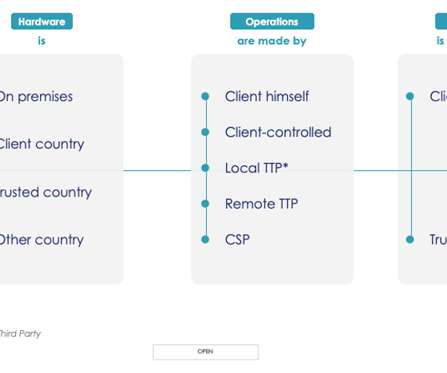
Thales Cloud Protection & Licensing
SEPTEMBER 13, 2022
Failed audits and cloud data breaches are common…. While there has been an improvement in enterprises using encryption to secure sensitive data in the cloud, this remains an area where continuous improvement and consolidation are necessary. See our eBook “ Achieve Digital Sovereignty with Thales for more on this.”.

Thales Cloud Protection & Licensing
MARCH 29, 2018
In the recent Thales eSecurity eBook, ‘ PCI Compliance and Data Protection for Dummies ’, we cover the main technologies that can be used, such as encryption and tokenization, to help with such efforts in protecting the payment prior to a successful authorization and secure storage of selected elements afterwards.

CyberSecurity Insiders
NOVEMBER 9, 2022
Protecting against malicious and accidental data exfiltration requires complete visibility into all encrypted data; both, while in motion and when at rest; along with a sophisticated DLP solution which can accurately identify, and protect it from exfiltration. Use these to communicate value and improvement to the C-suite.
Let's personalize your content